Table of Contents
Configuring LDAP for an application from the ground
I don't know if it is your case, but in mine, I have a BIG trouble when configuring a Jboss application to connect to LDAP (Active Directory). The documentation in the jboss website is not very detailed, and it appears as all the websites speak of well-know issues, so they don't detailed very much the steps need to be done to configure it.
In this page I will try to document every detail I did with a real-life application as an example: the JMX console.
From the ground
Version of Jboss: JBoss [The Oracle] 5.1.0.GA (build: SVNTag=JBoss_5_1_0_GA date=200905221053)
The community edition of JBoss is rare in terms of version: since one version to another, things can change, stop working, or God knows what other things can occurr. So I learned that the first step is to establish, withe in blank, the version of Jboss. Let's continue.
My application: JBOSS_HOME/server/default/deploy/jmx-console.war
From now on, when I speak of WEB-INF/jboss-web.xml, for instance, in fact I am speaking of JBOSS_HOME/server/default/deploy/jmx-console.war/WEB-INF/jboss-web.xml.
Step 0: have a walk on the LDAP side
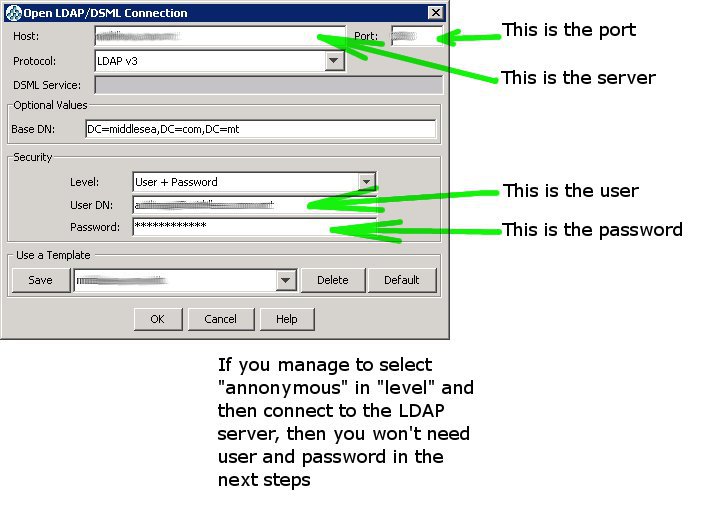
Install in your computer, or in the server, or whatever you want, an LDAP browser. You can install JXplorer (free software) or, if the LDAP server is Active Directory, you can install the “Admin Pack” of Microsoft.
To connect to the LDAP server you probably will need help from the administrator.
Ok, locate a group in the LDAP server –or create a new one– where the users belonging to this group are allowed to use the application. In my case I've selected the group “Admin_Group”.
Using Jxplorer you should know if you need to provide an user and a password to connect to he LDAP server or not (annonymous access). Keep this information to use later.
Step 1: Locate the login-config.xml file
This file is in JBOSS_HOME/server/xxx/conf. We have to provide values for this xml code:
<application-policy name="INVENT A NAME FOR THIS"> <authentication> <login-module flag="required" code="org.jboss.security.auth.spi.LdapExtLoginModule"> <module-option name="java.naming.factory.initial"> com.sun.jndi.ldap.LdapCtxFactory </module-option> <module-option name="java.naming.provider.url"> ldap://PUT THE SERVER : AND THE PORT ldap://example:3265 </module-option> <!-- step one: first connect (bind) to the ldap server --> <module-option name="java.naming.security.authentication">simple</module-option> <module-option name="bindDN">PUT A VALID USER TO CONNECT TO THE SERVER</module-option> <module-option name="bindCredential">PUT A VALID PASSWORD TO CONNECT TO THE SERVER</module-option> <!-- step two: second identify/validate the user --> <!-- Subrama del directorio activo desde la que comenzaremos la búsqueda --> <module-option name="baseCtxDN">PUT A VALUE HERE</module-option> <module-option name="baseFilter">(sAMAccountName={0})</module-option> <!-- step three: role search options --> <!-- we will locate for MiddleseaUser --> <module-option name="rolesCtxDN">PUT THE VALUE HERE</module-option> <module-option name="roleFilter">(member={1})</module-option> <module-option name="roleAttributeIsDN">true</module-option> <module-option name="roleNameAttributeID">name</module-option> </login-module> </authentication> </application-policy>
We will explain how to identify every one of the values needed to configure this XML snippet.
INVENT A NAME FOR THIS: It's just a name, we will use later. I've chosen for this ldapJMXConsole.
PUT THE SERVER : AND THE PORT: If you managed to connect to the LDAP server using Jxplore –I strongly recommend this even if you are using Active Directory in your installation–, this values are provided in the connection screen:
Step N: set a security domain
- Open WEB-INF/jboss-web.xml.
- Put the security-domain as is follows:
<security-domain>java:/jaas/ldapJMXConsole</security-domain>
Step N+1: Thing's aren't going well
Ok, let's face it: despite following the steps in this guide, thing's aren't working. The Active Directory Administrator isn't working very much (many times he/she is fighting in his/her own wars). And, what else???
Use the brute force to diagnose what is happening: Wireshark is a packet sniffer: it allows you to see what's happening behind the scenes. The problem I had to face when configuring this stuff was that there were no errors when the thing fails: nothing. No message, no error is in the server log, nothing.
But alas!!! with a packet sniffer you can see the traffic behind and the exact error message returnet.
If nobody allows you to install a packet sniffer in the production server (a bad idea), you can try to make a testing deployment in your computer and try to find there the correct configuration of the LDAP.